Tisalabs Knowledge Base
Social engineering attacks are facilitated by human psychology to manipulate individuals into divulging sensitive information or performing actions that benefit the attacker. In this tutorial, we'll explore a specific social engineering scenario known as the Fake Antivirus Software Scam. This scam aims to deceive users into purchasing fake antivirus software by exploiting their fear of malware and computer security threats.
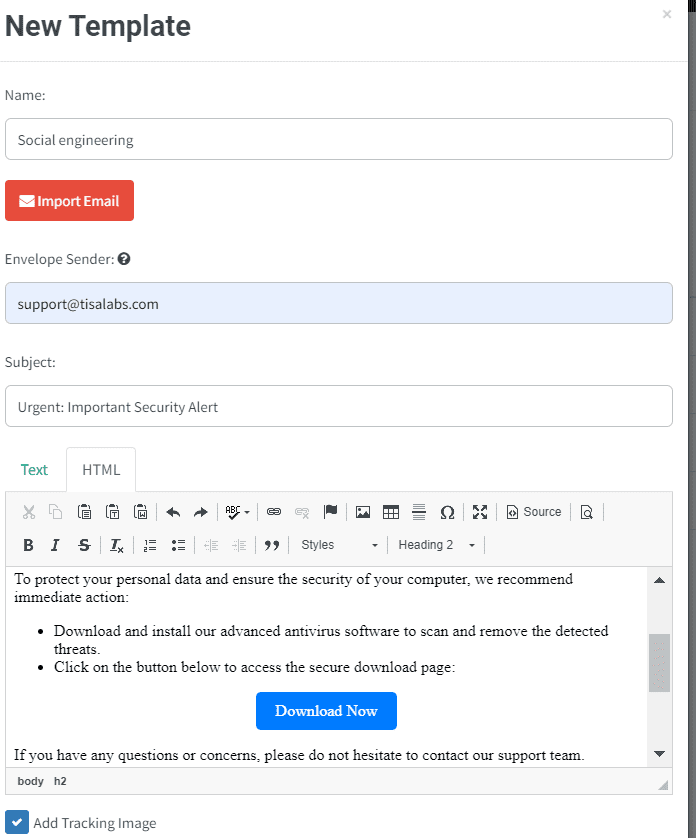
The first step involves creating a phishing email that entices recipients to click on a link leading to the fake antivirus software download page.
A persuasive email is designed that instills fear by warning recipients of malware infections and urges them to download the supposed antivirus solution.
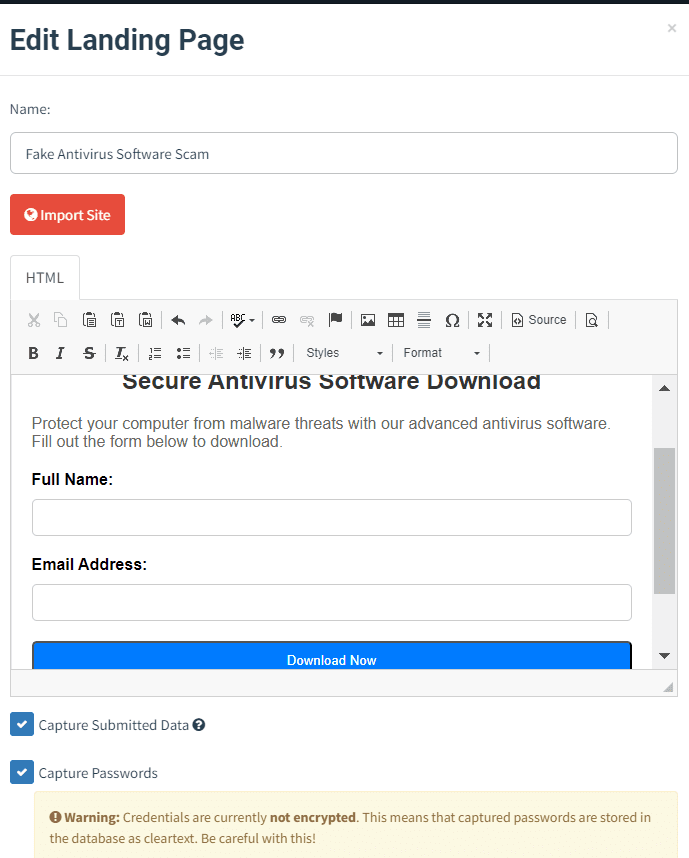
A convincing landing page is developed that mimics a legitimate antivirus software download site to deceive users into entering their information.
Step 1: Landing Page Creation A webpage resembling a reputable antivirus software vendor's site is developed, featuring download options and enticing visuals to encourage user interaction.
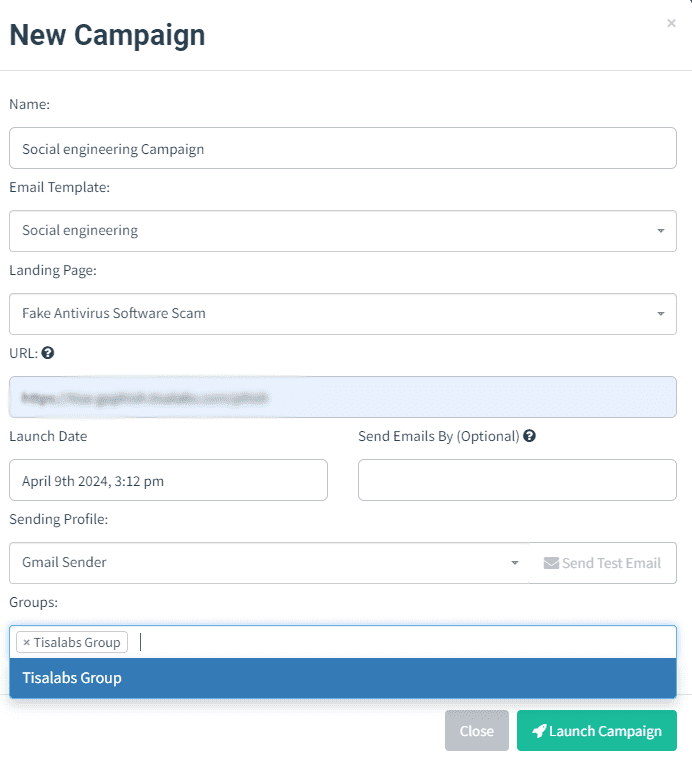
The phishing campaign is launched, and deceptive emails are sent out to targeted users.
Step 1: Campaign Launch The campaign is initiated, and its progress is monitored to track user interactions and email open rates.
Step 2: Campaign Progress Monitoring The campaign's progress will be monitored from the dashboard, tracking email open rates and user interactions.
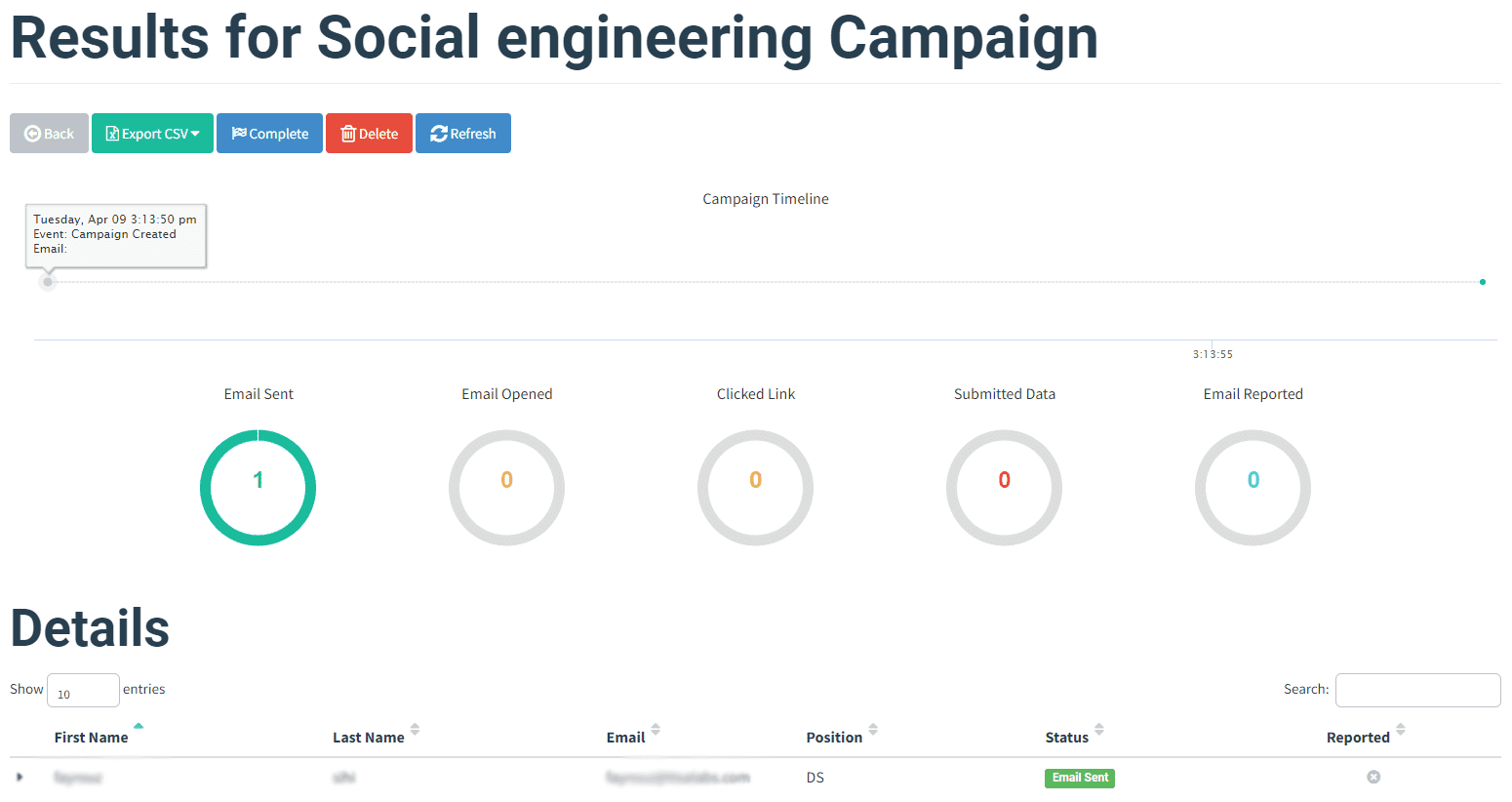
The campaign outcomes are evaluated by analyzing user interactions and collected data from the landing page submissions.
Step 1: User Interaction Analysis Recipient engagement with the phishing email and landing page is examined to assess the campaign's effectiveness.
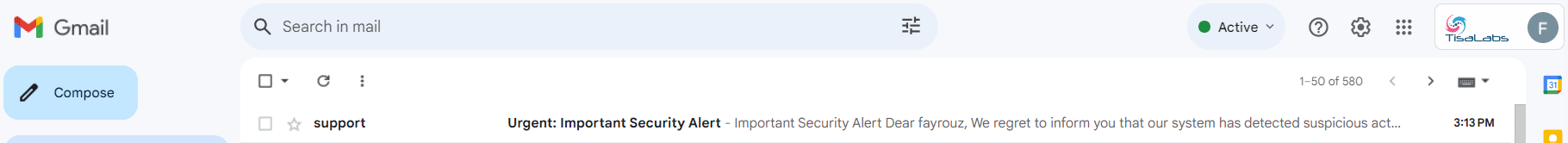
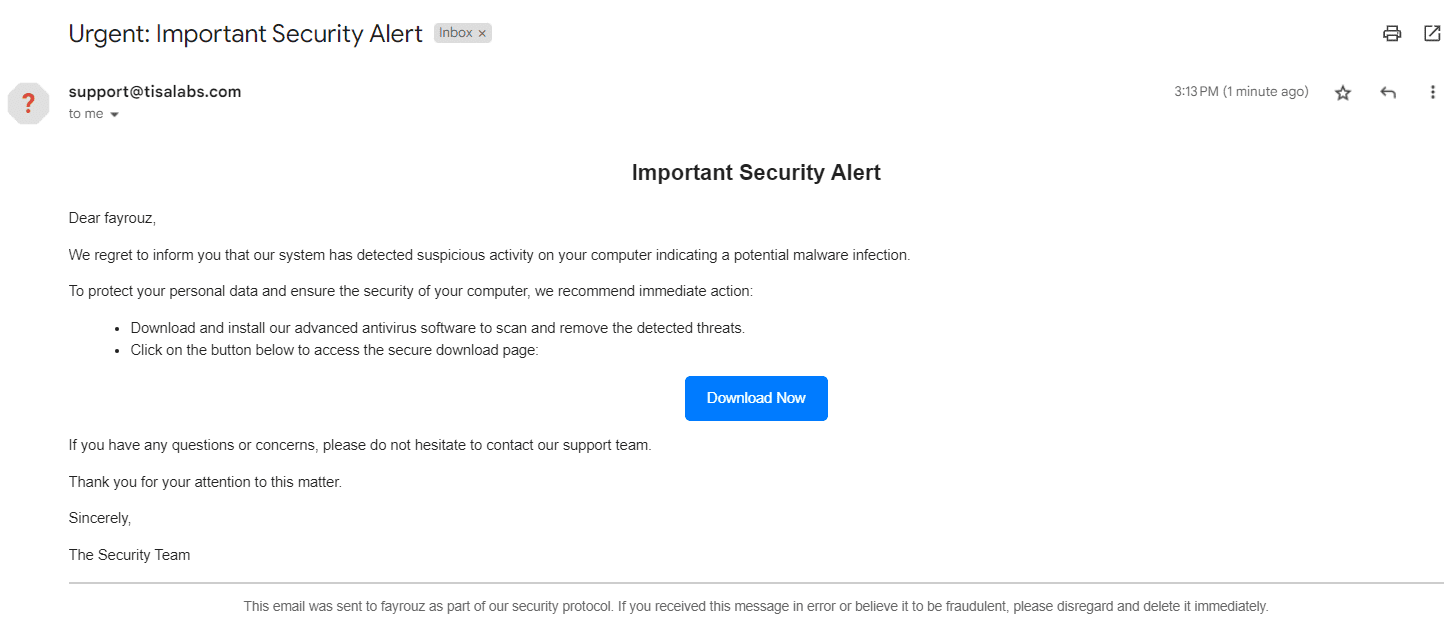
and this is the content of the email when the target user opens it:
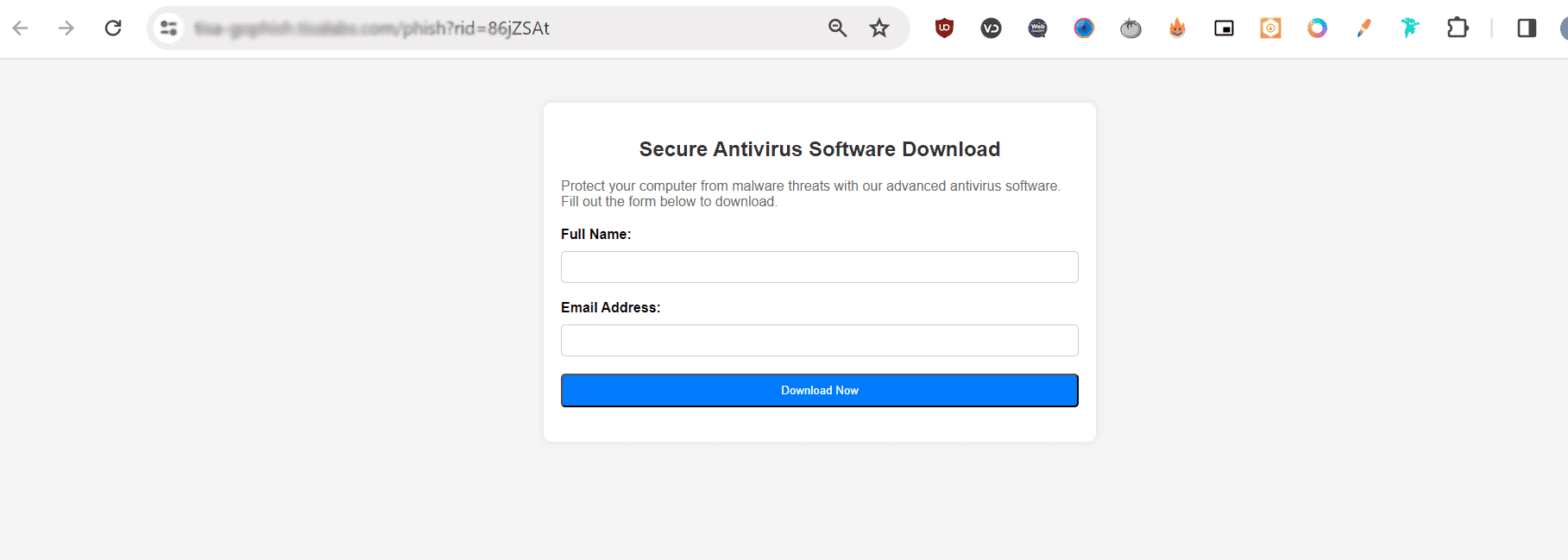
and this the content of the landing page that we did create to capture the data:
Step 2: Data Collection Review The submitted data is reviewed to understand the extent of user interaction and potential vulnerabilities exposed.
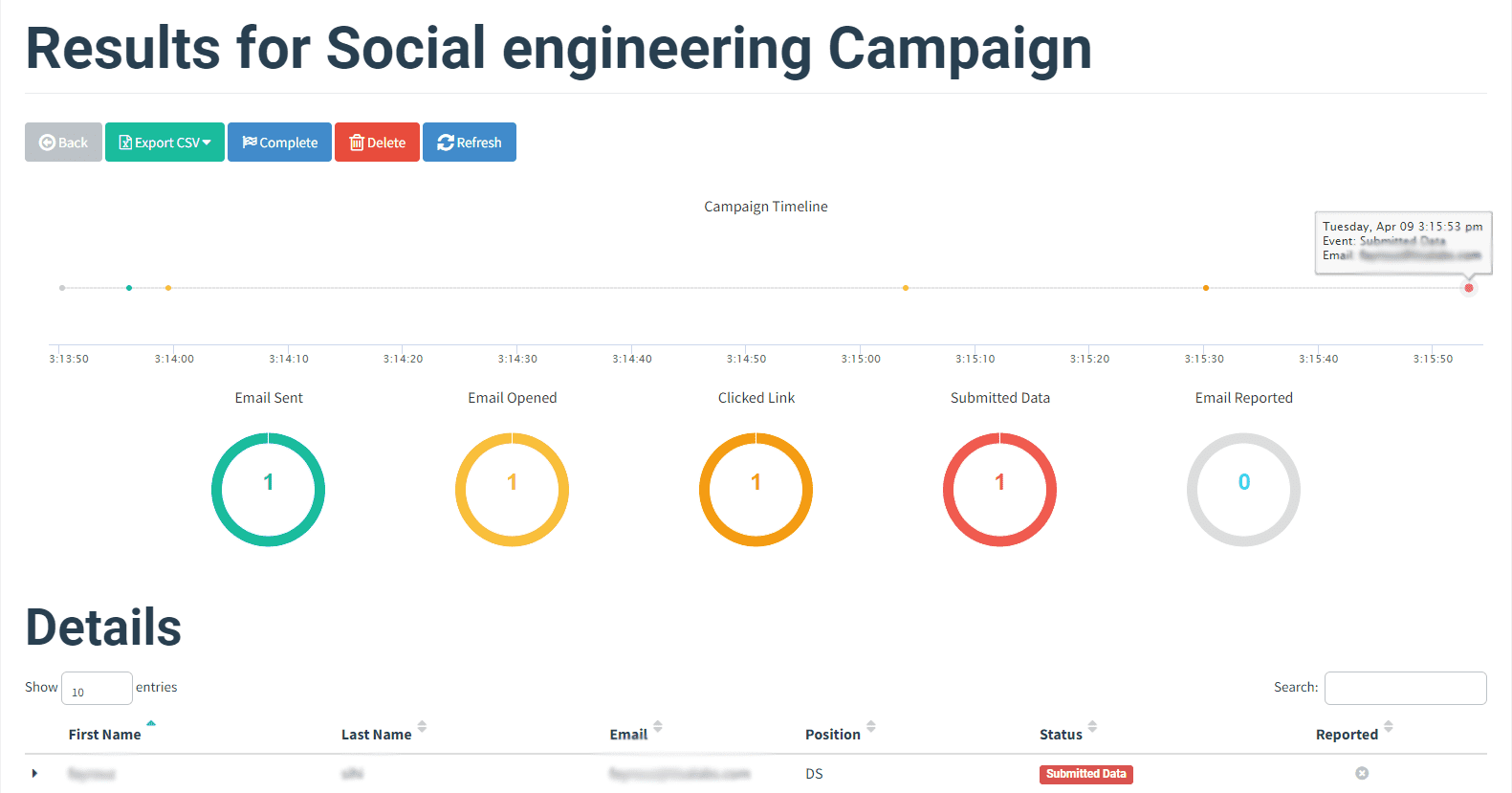
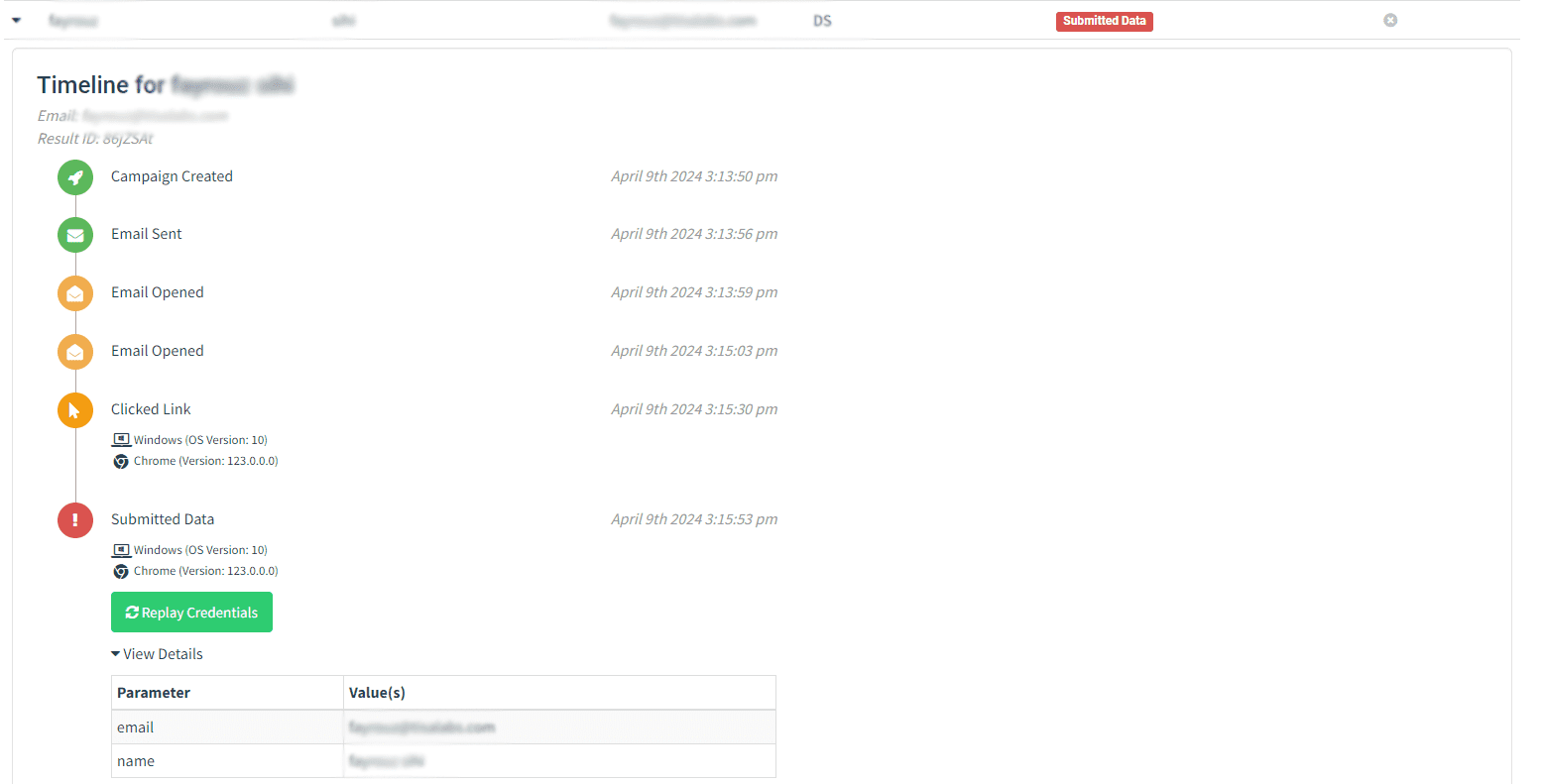
and following are the details of the data that we did capture using the form:
Users are educated about the risks associated with fake antivirus software scams and provided with guidance on identifying and avoiding such fraudulent schemes.
Step 1: Awareness Training Training sessions are conducted to raise awareness about social engineering scams and emphasize the importance of verifying software legitimacy before downloading.
Step 2: Security Best Practices The use of reputable antivirus software from trusted sources is encouraged, and users are advised to exercise caution when encountering unsolicited security warnings or offers.
By simulating a Fake Antivirus Software Scam, organizations can assess their susceptibility to social engineering attacks and implement appropriate security measures to mitigate risks. Vigilance, awareness, and proactive security measures are deemed essential in safeguarding against such deceptive tactics.
If you still can't find an answer to what you're looking for, or you have a specific question, open a new ticket and we'd be happy to help!
Contact Us